This challenge under the 'crypto' label was introduced to us by the following text:
0x00 intro
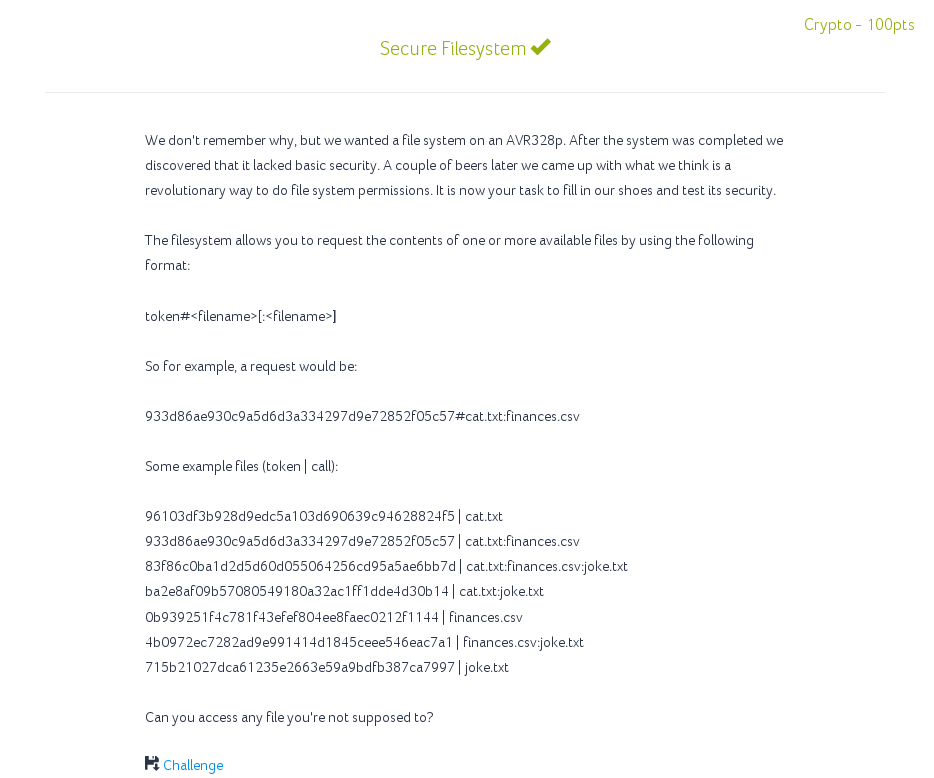
After flashing the encrypted hex to our rhme2 board we get the following on the serial console: RHMeOS file API Files in system:
drwxrwxr-x remote remote 4096 sep 1 .
drwxrwxr-x remote remote 4096 sep 1 ..
-r--r--r-- remote remote 87 sep 14 cat.txt
-r--r--r-- remote remote 47 sep 16 finances.csv
-r--r--r-- remote remote 3 sep 14 joke.txt
-rw------- root root 37 jan 5 passwd
-rw------- root root 8 jan 1 pepper
Request?
>>
If we try sending the sample string ( 933d86ae930c9a5d6d3a334297d9e72852f05c57#cat.txt:finances.csv) we get:
cat.txt:
A_A
(-.-)
|-|
/ \
| | __
| || | | \__
\_||_/_/
finances.csv:
year,profit
2014,+100%%
2015,+200%%
So it looks like we can ask not only for single files but for several files just by appending the requested filenames to the command string, preceded by ':'.
Of course, for this to work we must update the token at the beginning of the command. Otherwise the board just ignores us, showing no error when receiving incorrect tokens or malformed commands:
Request?
>> 933d86ae930c9a5d6d3a334297d9e72852f05c57#cat.txt:passwd
Request?
>>
0x01-- Length extension attack
Let's focus on the token then; it looks like a SHA-1 hash:
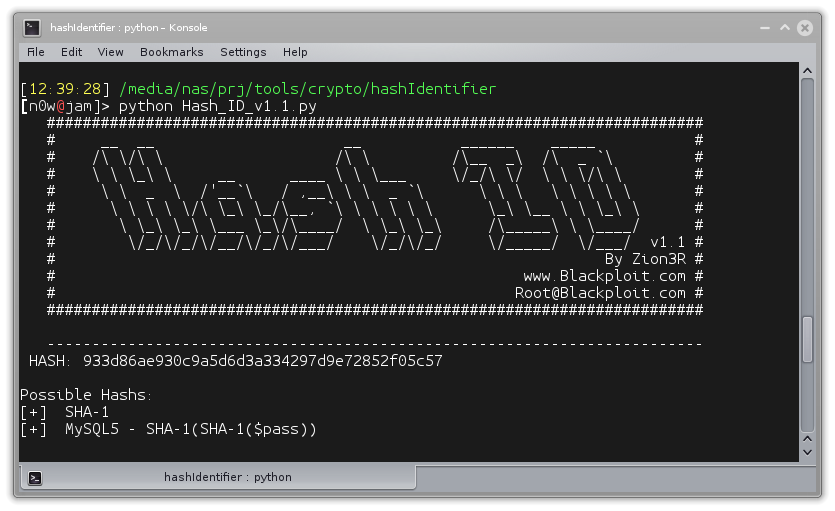
..so maybe we could read the contents of passwd by performing a length extension attack to compute a correct token given the proper key length (which we do not know).
From Wikipedia, on length extension attacks:
In cryptography and computer security, a length extension attack is a type of attack where an attacker can use Hash(message1) and the length of message1 to calculate Hash(message1 ∥ message2) for an attacker-controlled message2. This attack can be used to sign a message when a Merkle–Damgård based hash is misused as a message authentication code, allowing for inclusion of extra information.
This attack can be done on hashes with construction H(secret ∥ message)[1] when message and the length of secret is known. Algorithms like MD5, SHA-1, and SHA-2 that are based on the Merkle–Damgård construction are susceptible to this kind of attack.
From https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks:
An application is susceptible to a hash length extension attack if it prepends a secret value to a string, hashes it with a vulnerable algorithm, and entrusts the attacker with both the string and the hash, but not the secret. Then, the server relies on the secret to decide whether or not the data returned later is the same as the original data.
It turns out, even though the attacker doesn't know the value of the prepended secret, he can still generate a valid hash for {secret || data || attacker_controlled_data}! This is done by simply picking up where the hashing algorithm left off; it turns out, 100% of the state needed to continue a hash is in the output of most hashing algorithms! We simply load that state into the appropriate hash structure and continue hashing.
TL;DR: given a hash that is composed of a string with an unknown prefix, an attacker can append to the string and produce a new hash that still has the unknown prefix. The whole process is perfectly explained on the link above for those interested on the details (if you didn't know about this technique, now you do!).
There are several tools out there which perform this kind of attack, so I just picked one with python bindings and loop it over the keylength:
for i in range (0, 20):
hash, payload = (hashpumpy.hashpump(hashes[testRequest], testRequest, ':passwd', i))
currentPayload = payload
print ("-----------> i = %d" % i)
print ("-----------> Sending: {}".format(currentPayload))
time.sleep(0.2)
ser.write(buildPayload(hash, payload))
waitForPrompt()
ser.close()
sys.exit(0)
Running the whole script (which can be found here) yields:
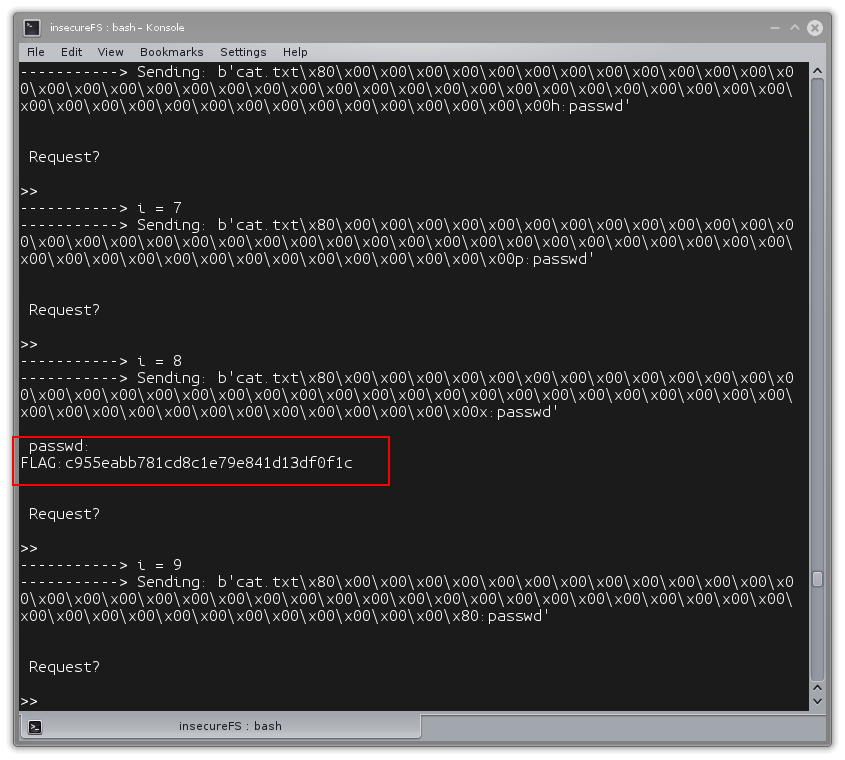
After retrieving the flag, I realized there was a hint on the filesize of pepper:
RHMeOS file API
Files in system:
drwxrwxr-x remote remote 4096 sep 1 .
drwxrwxr-x remote remote 4096 sep 1 ..
-r--r--r-- remote remote 87 sep 14 cat.txt
-r--r--r-- remote remote 47 sep 16 finances.csv
-r--r--r-- remote remote 3 sep 14 joke.txt
-rw------- root root 37 jan 5 passwd
-rw------- root root 8 jan 1 pepper
Request?
>>
..luckily both attack and bruteforce techniques were simple enough! :D